API Cyberattacks: What They Are, How They Happen, and How to Stop Them
Posted by: Prerna | August 01, 2024

Categories: API Security, API Development
Introduction
In the digital era, Application Programming Interfaces (APIs) play a pivotal role in enabling seamless communication and data exchange between different software applications and systems. However, the increased reliance on APIs has made them a prime target for cybercriminals seeking to exploit vulnerabilities and launch malicious attacks. This article delves into the world of API security, providing valuable insights into securing and protecting APIs from cyberattacks.
Understanding API Security
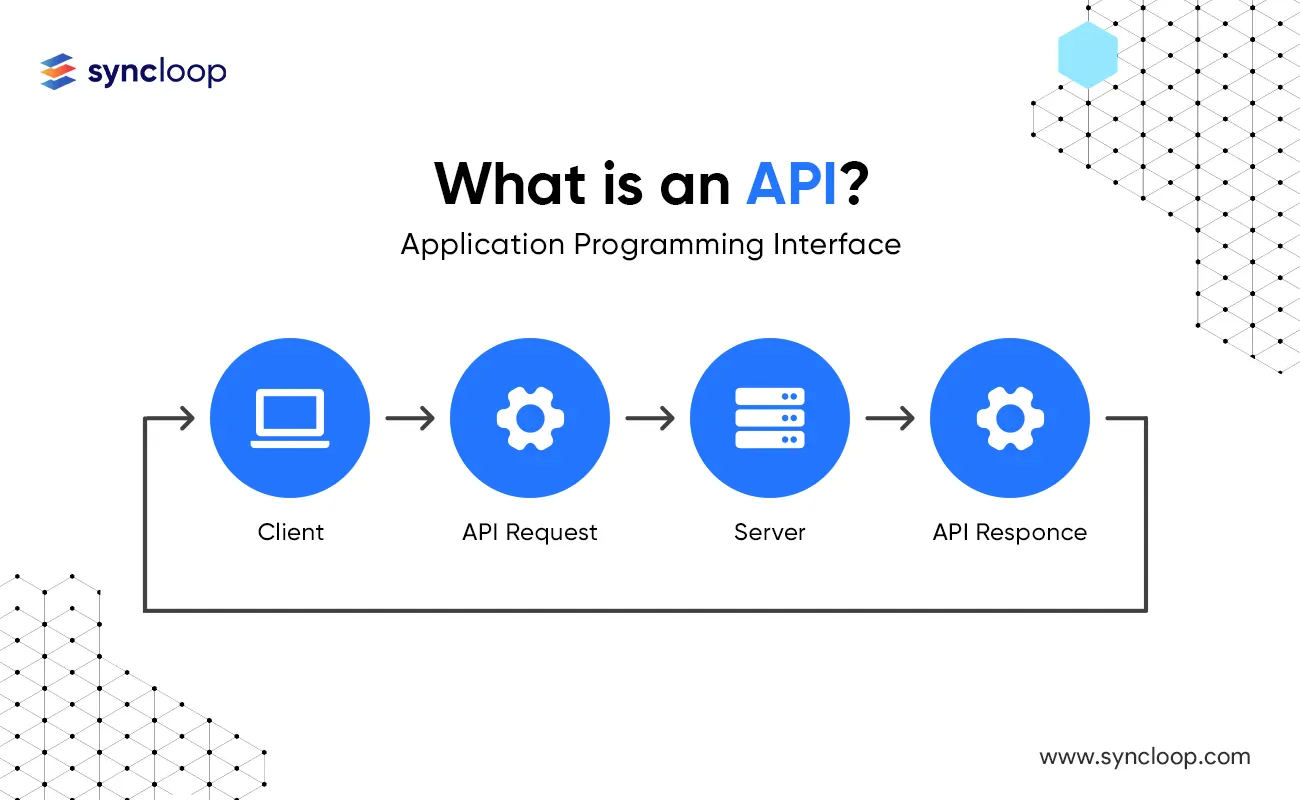
What are APIs?
APIs, or Application Programming Interfaces, are sets of protocols and tools that allow different software applications to communicate and interact with each other. They act as intermediaries, facilitating the exchange of data and functionality between diverse systems. APIs are utilized in various domains, including web services, mobile applications, cloud computing, and Internet of Things (IoT) devices.
Importance of API Security
APIs serve as a bridge between different applications, making them an attractive target for cyberattacks. A successful API breach can result in unauthorized access to sensitive data, manipulation of functionalities, and disruption of services. Therefore, robust API security is essential to safeguard the integrity, confidentiality, and availability of the data and services being exchanged.
Common Cyberattacks on APIs
API Key Attacks
API keys are alphanumeric codes used to authenticate and authorize access to APIs. Cybercriminals may attempt to steal or compromise these keys to gain unauthorized access to the API. Securing and rotating API keys regularly can mitigate such attacks.
Injection Attacks
Injection attacks involve injecting malicious code, such as SQL, NoSQL, or OS commands, into API requests. Proper input validation and parameterized queries are crucial to prevent injection vulnerabilities.
Cross-Site Scripting (XSS) Attacks
XSS attacks occur when attackers inject malicious scripts into web applications that are subsequently executed by unsuspecting users. Implementing output encoding and validating user input can thwart XSS attacks.
Man-in-the-Middle (MitM) Attacks
MitM attacks intercept communication between clients and APIs to eavesdrop or manipulate data. Encrypting data in transit using protocols like HTTPS can prevent MitM attacks.
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks
DoS and DDoS attacks overload API servers, causing service disruptions. Implementing rate limiting and using specialized tools like Web Application Firewalls (WAFs) can mitigate the impact of these attacks.
Best Practices for Securing APIs
Use Strong Authentication and Authorization
Implement robust authentication mechanisms, such as OAuth or API tokens, to verify the identity of users and applications accessing the API. Additionally, employ granular authorization controls to restrict access based on user roles and privileges.
Implement Rate Limiting
Enforce rate limits on API requests to prevent abuse and overloading of resources. Rate limiting helps maintain optimal API performance and protects against DoS and DDoS attacks.
Encrypt Data in Transit and at Rest
Use industry-standard encryption protocols like TLS/SSL to protect data transmitted between clients and the API. Furthermore, encrypt sensitive data stored within the API or its underlying databases to safeguard against data breaches.
Regularly Monitor and Audit APIs
Monitor API traffic and logs to detect suspicious activities and potential security breaches. Conduct regular security audits to identify vulnerabilities and address them promptly.
Keep APIs Updated and Patched
Stay up-to-date with the latest security patches and updates for the API and its dependencies. Outdated software may contain known vulnerabilities that can be exploited by attackers.
Use Web Application Firewalls (WAFs)
Deploy WAFs to protect APIs from a wide range of cyber threats, including SQL injection, XSS, and DoS attacks. WAFs act as a barrier between clients and the API, inspecting and filtering incoming traffic for potential threats.
Employ Proper Error Handling
Implement proper error handling mechanisms to prevent the leakage of sensitive information in error messages. Error messages should be informative to developers while being vague to potential attackers.
API Security Testing and Penetration Testing
Regularly conduct security testing on APIs, including penetration testing, to identify and remediate vulnerabilities proactively. Testing should cover various attack scenarios and use cases.
Secure Coding Practices for API Developers
Input Validation
Sanitize and validate all input data received by the API to prevent injection attacks and other input-based vulnerabilities.
Parameterized Queries
Use parameterized queries to interact with databases, avoiding the risk of SQL injection attacks.
Role-Based Access Control
Implement role-based access control to ensure that only authorized users can access specific API functionalities.
Output Encoding
Encode output data to prevent XSS attacks and ensure that user-generated content is safe.
Secure Logging and Error Handling
Adopt secure logging practices to avoid exposing sensitive information in logs, and handle errors gracefully to avoid information leakage.
Sanitization of User Input
Thoroughly sanitize user inputs to prevent code injection and malicious content from affecting the API.
API Security Tools and Solutions
API Gateways
API gateways act as intermediaries between clients and APIs, providing security features like authentication, rate limiting, and traffic filtering.
API Security Platforms
Dedicated API security platforms offer comprehensive protection against a wide array of API threats and vulnerabilities.
Web Application Firewalls (WAFs)
WAFs safeguard APIs from common web-based attacks and help ensure continuous service availability.
Security Information and Event Management (SIEM) Systems
SIEM systems provide real-time monitoring and threat detection for APIs, enabling swift responses to potential security incidents.
Educating Your Development Team on API Security
Educating developers about the best practices and the latest security trends in API development is essential. Regular training sessions and workshops can empower the team to build secure APIs.
The Future of API Security
As technology evolves, so will the threats to API security. Embracing emerging security practices, leveraging AI and machine learning for threat detection, and fostering a security-conscious culture will be crucial for safeguarding APIs in the future.
Conclusion
Securing and protecting APIs from cyberattacks is paramount in today's interconnected digital landscape. By following best practices, employing the right security tools, and educating development teams, organizations can ensure the integrity and reliability of their APIs. API security should be an integral part of any application development process, enabling businesses to build trust with their users and stakeholders.
Back to Blogs