API Security in a Microservices Architecture: Securing Communication Between Microservices
Posted by: Deepak | April 02, 2024
Categories: API Development, Microservice Architecture, API Security
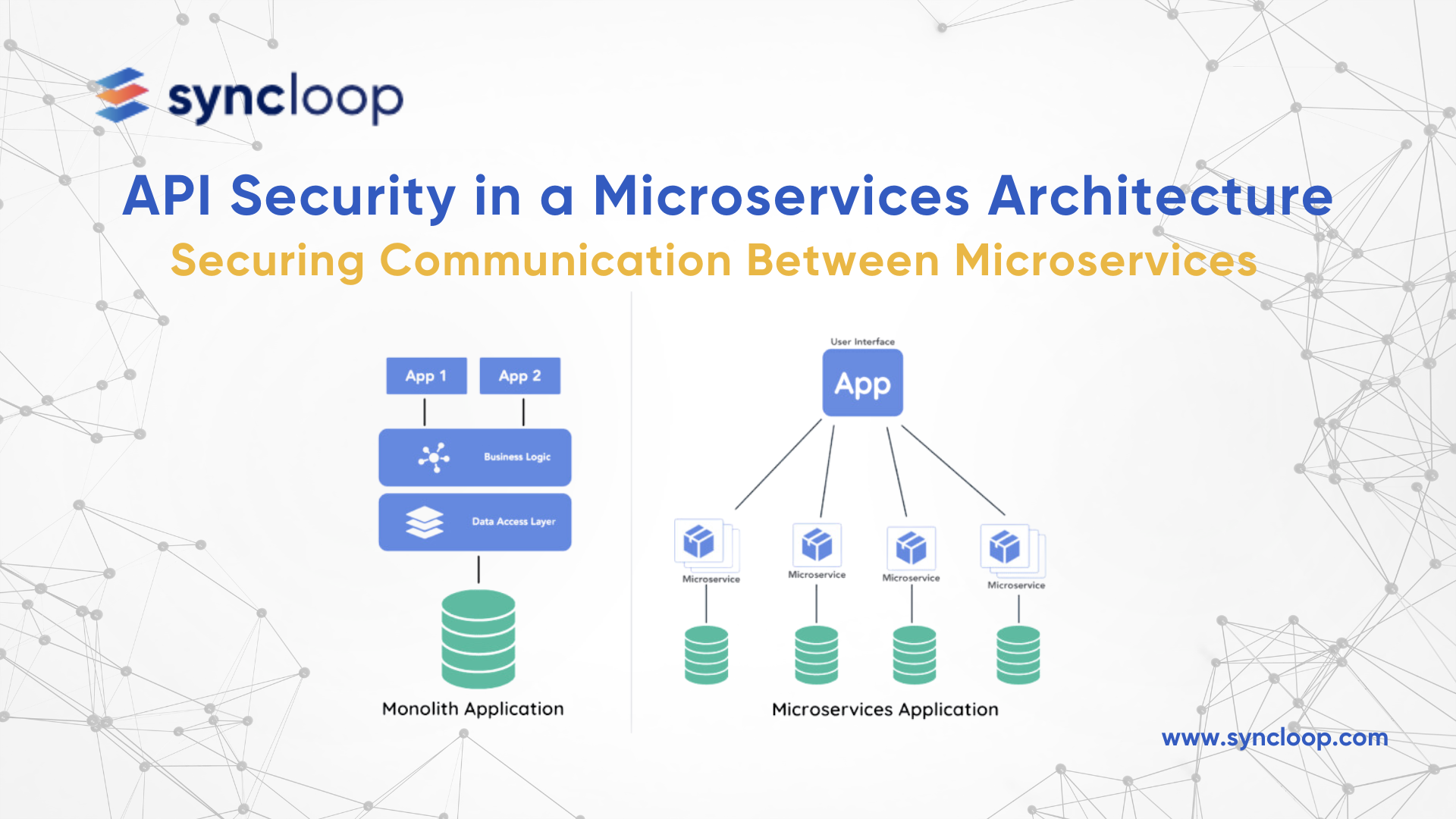
The rise of microservices architecture has revolutionized application development. By breaking down monolithic applications into smaller, independent services, microservices offer increased scalability, agility, and fault tolerance. However, this distributed nature introduces new security challenges, particularly in securing communication between these microservices.
This blog delves into the intricacies of API security in a microservices architecture. We'll explore the security threats, best practices, and latest tools and technologies to safeguard communication between your microservices.
The Challenge: Increased Attack Surface in Microservices
While microservices offer numerous advantages, their distributed nature creates a vastly expanded attack surface. Traditional monolithic applications have a single point of entry, making security measures more straightforward. In contrast, microservices communicate through APIs, creating numerous potential entry points for attackers.
Here are some key security concerns in microservices architecture:
- Increased Network Traffic: The constant communication between microservices generates significant network traffic. Malicious actors can exploit this by injecting unauthorized requests or eavesdropping on communication to steal sensitive data.
- Fragmented Authentication and Authorization: Traditional session-based authentication becomes less effective in a stateless microservices environment. Implementing robust authentication and authorization mechanisms for each microservice API is crucial.
- API Abuse and Exploits: Unsecured APIs are vulnerable to brute-force attacks, denial-of-service attacks (DoS), and zero-day exploits.
Statistics paint a concerning picture. According to a report by Positive Technologies, API security incidents grew by a staggering 338% in 2022. This highlights the urgent need for robust API security measures in microservices architecture.
Securing Microservice Communication: Best Practices
Here are some best practices to ensure secure communication between your microservices:
- Embrace Encryption (HTTPS): Enforce HTTPS communication for all API interactions between microservices. This encrypts data in transit, protecting it from eavesdropping and tampering.
- Implement Mutual Authentication: Employ mutual authentication techniques like certificates or tokens to verify the identity of both the service making the request and the service receiving it. This prevents unauthorized access to APIs.
- Adopt Zero Trust Architecture: Zero Trust principles assume no inherent trust within the network. Implement strong authentication and authorization checks for every API call, regardless of its source.
- Leverage API Gateways: Utilize an API Gateway as a single entry point for all API requests. This allows centralized security policies like authentication, authorization, rate limiting, and API monitoring to be enforced efficiently.
Tools and Technologies for Microservice API Security
The security landscape is constantly evolving, offering various tools and technologies to bolster API security in a microservices environment:
- API Security Platforms: Dedicated API security platforms like Apigee, Kong, and Auth0 offer comprehensive solutions for managing API lifecycles, including access control, threat protection, and API analytics.
- Service Meshes: Service meshes like Istio and Linkerd manage API traffic between microservices. They can enforce security policies like authentication and authorization at the network layer.
- Cloud-Native Security Solutions: Cloud providers like AWS, Azure, and GCP offer managed security services specifically designed for microservices architectures. These can include identity and access management (IAM) solutions, security information and event management (SIEM) tools, and cloud workload protection platforms (CWPP).
Integration Process and Benefits for Different Industries
The integration process for API security tools and technologies will vary depending on your specific infrastructure and chosen tools. However, some general steps can be followed:
- Identify Security Requirements: Assess your security needs and identify sensitive data flows between microservices.
- Select Security Tools: Choose the appropriate tools and technologies based on your requirements and expertise. Cloud-managed solutions offer faster deployment, while self-hosted options provide greater control.
- Configure and Deploy: Configure security policies within the chosen tools and integrate them with your existing microservices architecture.
- Monitoring and Optimization: Continuously monitor API activity for suspicious behavior and optimize security policies based on usage patterns.
Here are some industry-specific benefits of implementing robust API security in a microservices architecture:
- Financial Services: Enhanced data protection for sensitive financial information like account details and transaction data. Improved compliance with regulations like PCI-DSS.
- Healthcare: Secure patient data exchange between healthcare applications and ensure HIPAA compliance.
- Retail: Protect customer data and prevent fraudulent transactions in e-commerce environments.
Use Cases and Real-World Applications
Here are some real-world use cases of API security in a microservices architecture:
- A travel booking platform: Uses API security measures like OAuth 2.0 and OpenID Connect to authenticate users and authorize access to booking information across various microservices like flight search, hotel booking, and payment processing.
- A healthcare provider: Enforces X.509 client certificates for secure communication between a patient portal application and backend microservices handling electronic health records (EHR).
- An e-commerce platform: Implements API rate limiting to prevent denial-of-service attacks targeting product availability and order processing APIs.
Advantages and Disadvantages of API Security Tools
While API security tools offer significant benefits, there are also some drawbacks to consider:
Advantages
- Centralized Management: Simplifies security policy enforcement across all microservices.
- Improved Visibility: Provides insights into API usage patterns and potential security threats.
- Reduced Development Time: Streamlines API security implementation, allowing developers to focus on core functionalities.
Disadvantages
- Increased Complexity: Introducing additional tools can add complexity to your microservices architecture.
- Vendor Lock-in: Choosing a specific platform might lead to vendor lock-in, making it difficult to switch providers in the future.
- Cost Considerations: Cloud-managed security solutions can incur ongoing subscription costs.
Conclusion
In conclusion, API security is paramount in a microservices architecture. The increased attack surface necessitates robust security measures to protect sensitive data and prevent unauthorized access. By implementing best practices, leveraging security tools and technologies, and following a well-defined integration process, you can ensure secure communication between your microservices. Remember, a secure microservices architecture is essential for building trust with your users and protecting your valuable data assets.
Back to Blogs